Threat Mitigation in Containerized Environments
Keywords:
Container Security, Threat Mitigation, Containerized Environments, Docker SecurityAbstract
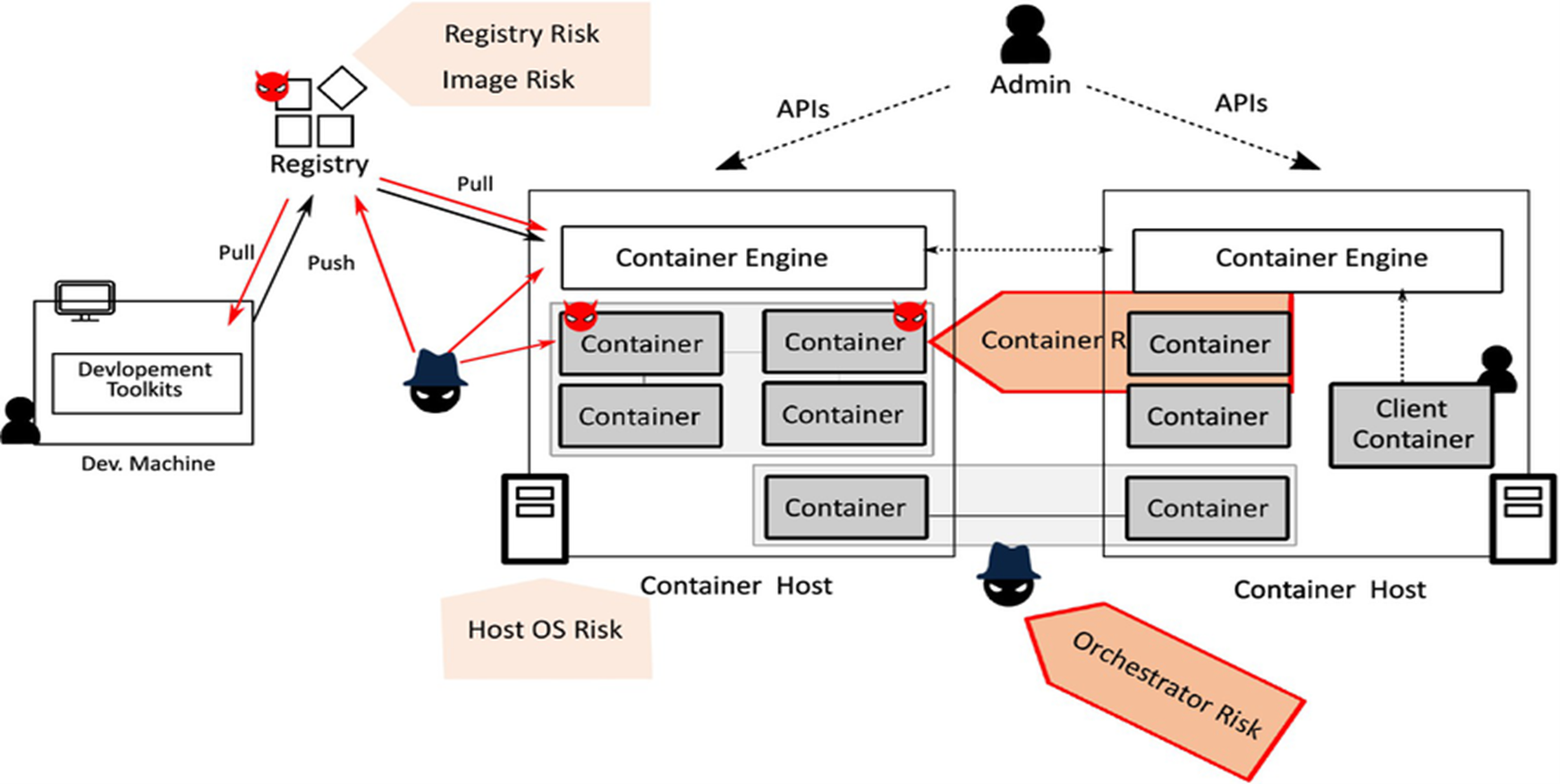
Containerized environments have revolutionized application development and deployment, offering unmatched flexibility, scalability, and consistency across diverse infrastructures. However, these environments also introduce unique security challenges, stemming from the shared nature of resources, the immutability of container images, and the complexities of container orchestration platforms like Docker and Kubernetes. This paper provides an in-depth exploration of the threat landscape within containerized environments, focusing on key areas such as container escape, image vulnerabilities, network attacks, and supply chain risks. We also discuss robust mitigation strategies, including the use of hardened images, network segmentation, and container-specific security tools. The analysis culminates in a set of best practices aimed at securing containerized environments against evolving threats.
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 Applied Research in Artificial Intelligence and Cloud Computing

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.