UNCOVERING EVIDENCE OF ATTACKER BEHAVIOR ON THE NETWORK
Keywords:
Cybersecurity, Internet of Things, Man-in-the-middle (MitM) Attacks, Intrusion Detection Systems, Signature-Based Intrusion Detection Systems, Signature-Based, Anomaly-Based Detection, Machine Learning, Convolutional Neural Network (CNN), Anomaly-based IDS models, intrusion detection systems (IDS), signature-based intrusion detection systems (SIDS), tactics, techniques, Distributed Denial-of-Service (DDoS), Support Vector ClassifierAbstract
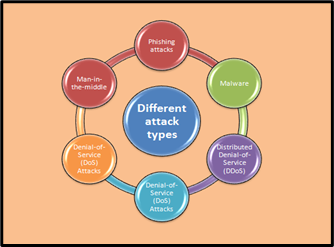
This comprehensive research presents and investigates a diverse assessment of interruption discovery strategies and their job in contemporary online protection. Interruption Recognition Frameworks are taken apart as vital parts in defending computerized foundations, utilizing different techniques, for example, signature-based, peculiarity based, and heuristic-based identification. While signature-based strategies demonstrate strong against known dangers, the review highlights the urgent job of irregularity-based and heuristic-based approaches in countering novel and complex assaults. Different types attract, their characteristics and behaviors has explored in this paper. The mix of AI and Man-made consciousness (computer based intelligence) in recognizing odd exercises arises as an extraordinary power, empowering versatile reactions to developing digital dangers. The exploration fundamentally breaks down the difficulties looked by existing location strategies, including versatility concerns, high bogus positive rates, and the encryption-related obstacles in rush hour gridlock examination. The outcomes and investigation segment approves the viability of proposed models, including group learning strategies and creative techniques, for example, the Solid Methodology in light of Blockchain and Peculiarity based location (SABA). A Convolutional Brain Organization (CNN) model for interruption location in IoT conditions and a cross breed approach joining positioning based channel strategies and NSGA-II exhibit eminent exactnesses. The review's suggestions for network security are significant, prompting proposals for a TTP-driven approach, mix of conduct peculiarities, persistent security mindfulness preparing, standard red group works out, versatile episode reaction plans, and intermittent security reviews. By and large, the examination contributes a nuanced comprehension of assailant's ways of behaving, down to earth procedures for online protection flexibility, and makes way for future investigation into dynamic danger scenes and the human component in network safety.
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2020 Authors

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.




